10 Best Games for Teenage Girls to Play On Android Smartphones
Games for Teenage Girls to Play On Android Smartphones Games are expressions and an exuberant ride to another dimension. It…
What is MICR? – Definition, Quality, Benefits, and More
MICR Definition Magnetic ink character recognition code, known as MICR, is a character-recognition technology used mainly by the banking industry….
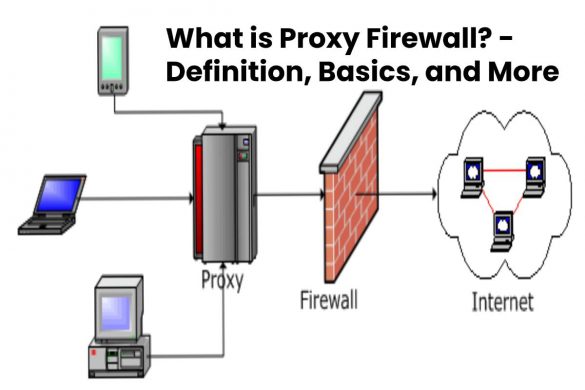
What is Proxy Firewall? – Definition, Basics, and More
Proxy Firewall Definition In contrast to a packet-oriented firewall, a Proxy Firewall can monitor and filter communication at the application…
What is FirePass? – Definition, Benefits, Uses and More
FirePass Definition The FirePass is F5’s VPN / SSL solution. It comes in the form of a rackable appliance (1u…
What is GISP Certification? – Definition, Steps to Access and More
GISP Certification The GISP certification is recognized internationally, is independent of the software, and is available to geospatial professionals around…
What is RPZ (Response Policy Zones)? – Definition, Advantages and More
RPZ Definition RPZ (Response Policy Zones) is one of the DNS filtering functions for preventing connection to specific nodes such…
What is Digital Watermarking? – Definition, Features and More
Digital Watermarking Definition Digital Watermarking is a technique that hides information and part of the known as steganographic. (steganography is…
How to Generate Sales Report in Shopify? – Mipler
Are you looking to create a sales report? Or perhaps a tax report? Mipler has a solution for you. Think about…
7 Types Of Instagram Content You Should Be Creating In 2025
Instagram Content you Should be Creating in 2024 Business owners struggle to come up with Instagram content because they feel…
The role of data leadership in data transformation [2025]
Introduction Data transformation – Data leadership plays a vital role in modern businesses in the digital era. Data leaders are…
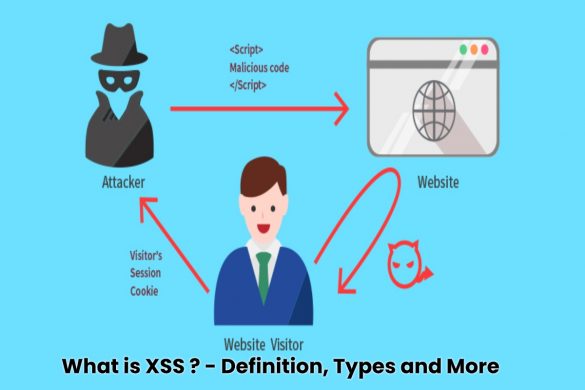
What is XSS (Cross-site Scripting)? – Definition, Types and More
What is XSS? XSS (Cross-site Scripting) is a code injection attack that allows an attacker to execute a malicious script…
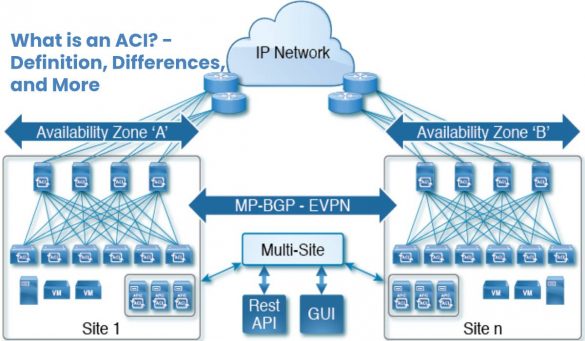
What is an ACI? – Definition, Differences, and More
ACI Definition With ACI (Application Centric Infrastructure), the data center network can be optimized-including components from other manufacturers. The design…
Recent Posts
Importance of Test Automation in Continuous Testing
Automation Testing Things are expected to change in the agile and DevOps environment. Organizations are transforming people, processes, and technologies…
Optimizing Performance: Tips for Speedy Flutter Apps
Introduction In the fast-paced world of mobile application development, user experience is paramount. As developers strive to create feature-rich and…