Kamran Sharief
What is AES? – Definition, Features, Uses and More
AES Definition The AES (Advanced Encryption Standard) is one of the most common methods of encrypting essential data, which organizations…
Want to become a photographer? Here’s what you should know
How to Become a Photographer? Is photography a profession or a hobby? Of all the careers and hobbies that exist,…
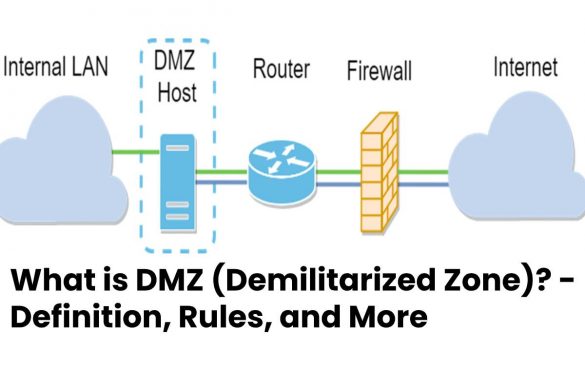
What is DMZ (Demilitarized Zone)? – Definition, Rules, and More
DMZ Definition The DMZ (Demilitarized Zone) is an independent network that acts as a buffer zone between an external network…
What is TLS Certificate? – Definition, Uses and More
TLS Certificate Definition The TLS Certificate (Transport Layer Security) is a data encryption protocol to provide security in unsafe environments….
Ultra High Tech Vaporizer – The Yocan Hit
Yocan Hit Vaporizer: Release your stifled energy with this La Mode dry vaporizer that’s one of its kind. This new…
What is a AxCrypt? – Definition, Characteristics and More
AxCrypt Definition AxCrypt is a security utility that allows you to protect the confidentiality of files. The introduction of it…
Richard Liu Expands JD.com Services to IoT Smart Home Technology
Home Improvement Technologies Richard Liu understands how the Internet of Things (IoT) is taking a foothold on technology. Also the…
What is an iCloud Keychain? – Definition, Uses and More
What is an iCloud Keychain? The iCloud Keychain was announced at WWDC 2013, along with OS X Mavericks and iOS…
Zen Reborn Babies can improve Digital Marketing
Babies are really fond of their Zen Reborn Dolls that will give them lots of choices through digital marketing strategies….
Make sure your smart TV isn’t watching you with these security tips
Smart TV Security Tips Today, TVs are highly evolved machines capable of accomplishing tasks you’d associate with a computer. Further,…
Follow the tips to convert the videos from MP4 to WMV
Oh! This video is not working in your phone. You need to then look for the file extension details first…
Bobblehead collections give you extra profits!
We all want to have a profitable business. This happens to all of us that want to invest our money…